Rapid7 - insightIDR
Manufacturer's warranty .
SMS notification .
Return and exchange .
Different payment methods .
Best price .
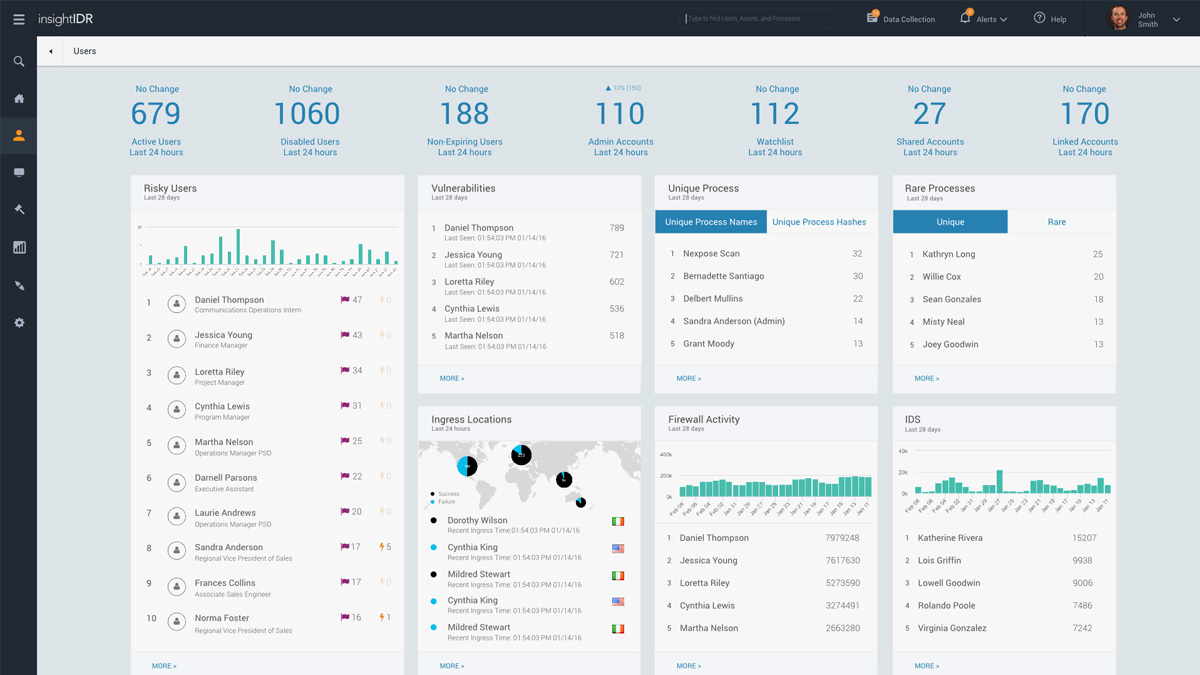
User Behavior Analytics
In 2017, 80% of hacking-related breaches used either stolen passwords and/or weak or guessable passwords, per the Verizon DBIR. Attackers are compromising assets not only via malware, but by moving laterally between them using credentials stolen by traffic manipulation, hash extraction, and other techniques. By continuously baselining healthy user activity in your organization, InsightIDR extends beyond defined indicators of compromise to reliably detect attackers masking as company employees.
Attacker Behavior Analytics
Attacks are a human problem. They're caused by humans, and they can only be truly defeated by humans. The expert analysts working in our SOCs live and breathe attacker behavior every day. As they identify new threats, they're looking for signs that can help detect such activity in the future, even earlier in the attack chain. We're constantly turning their knowledge into useful, actionable detections known as Attacker Behavior Analytics. The best part? ABA is available in InsightIDR.
Endpoint Detection and Visibility
From our continuous research on attacker behavior, we understand just how frequently endpoints are exploited and the magnitude of work it takes to monitor them—especially when employees are off your corporate network. That’s why InsightIDR comes standard with a cross-product, universal Insight Agent and endpoint scanning, giving you real-time detection and the ability to proactively hunt for answers.
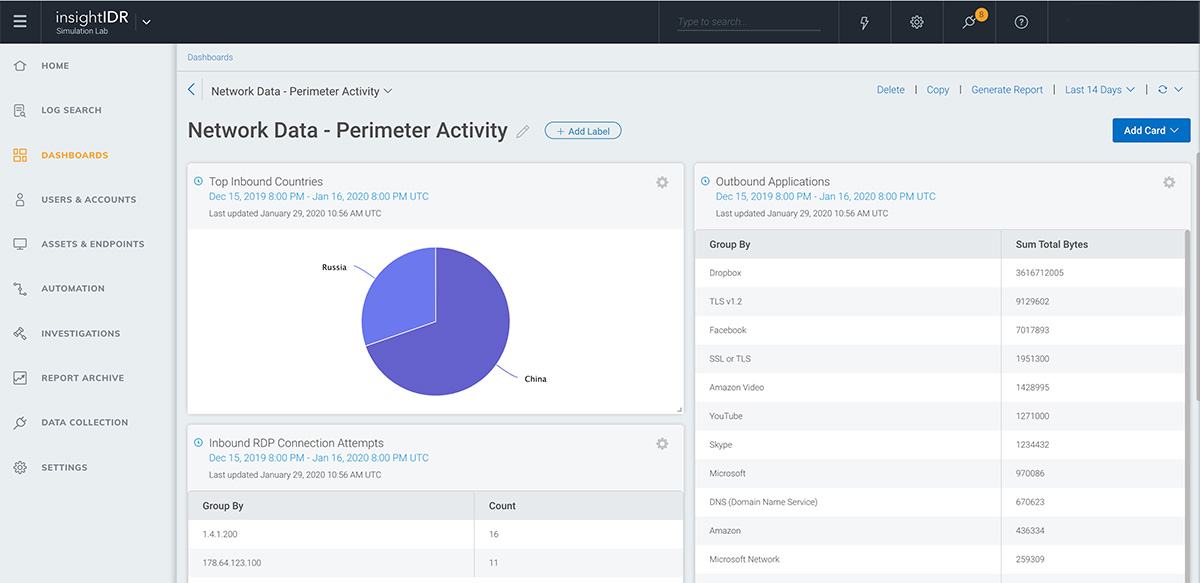
Network Traffic Analysis
Rapid7 is excited to announce that Network Traffic Analysis is available for InsightIDR customers. Rapid7 acquired NetFort, a leading provider of security analytics and automation, in Spring 2019. This functionality represents the first wave of new capabilities fueled by NetFort technology into the Insight platform.
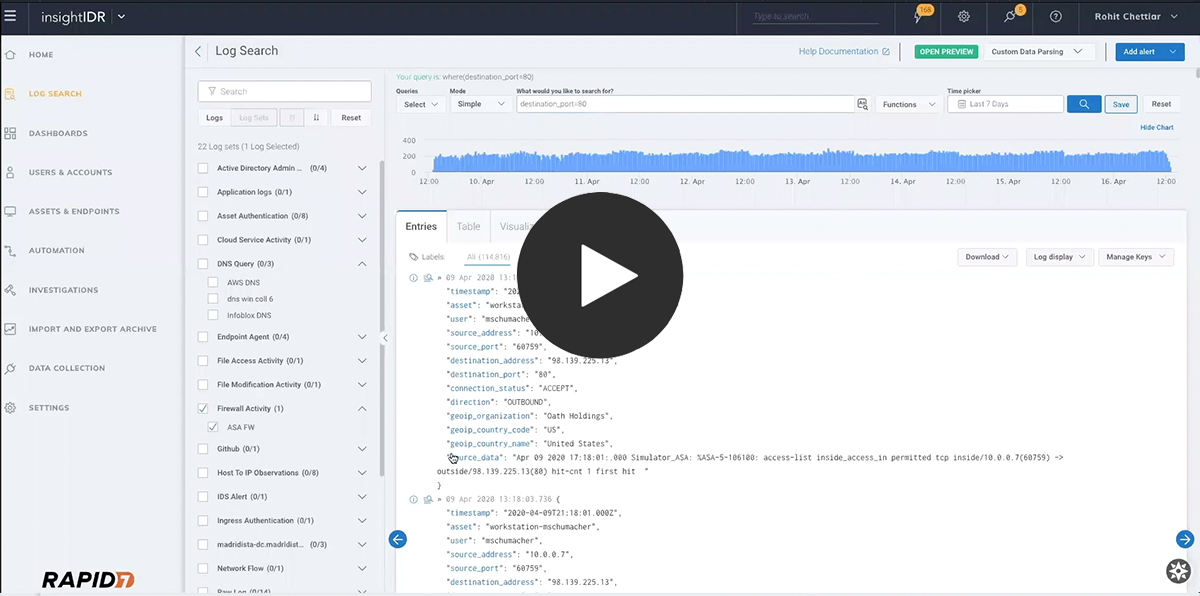
Centralized Log Management
Cross endlessly searching logs, writing convoluted queries, and hiring certified data splunkers off your to-do list. InsightIDR correlates the millions of daily events in your environment directly to the users and assets behind them to highlight risk across your organization and prioritize where to search. And our cloud-based architecture behind the Rapid7 Insight platform delivers a smooth search across your logs and automates compliance without worrying about racks of hardware. Learn more about log storage and retention in InsightIDR.
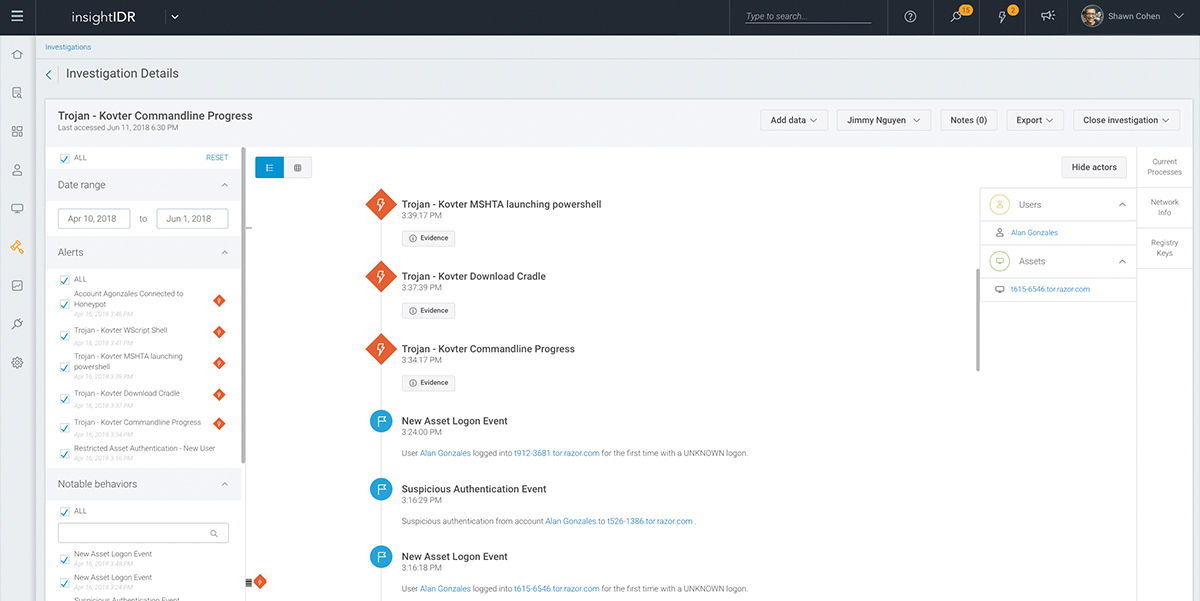
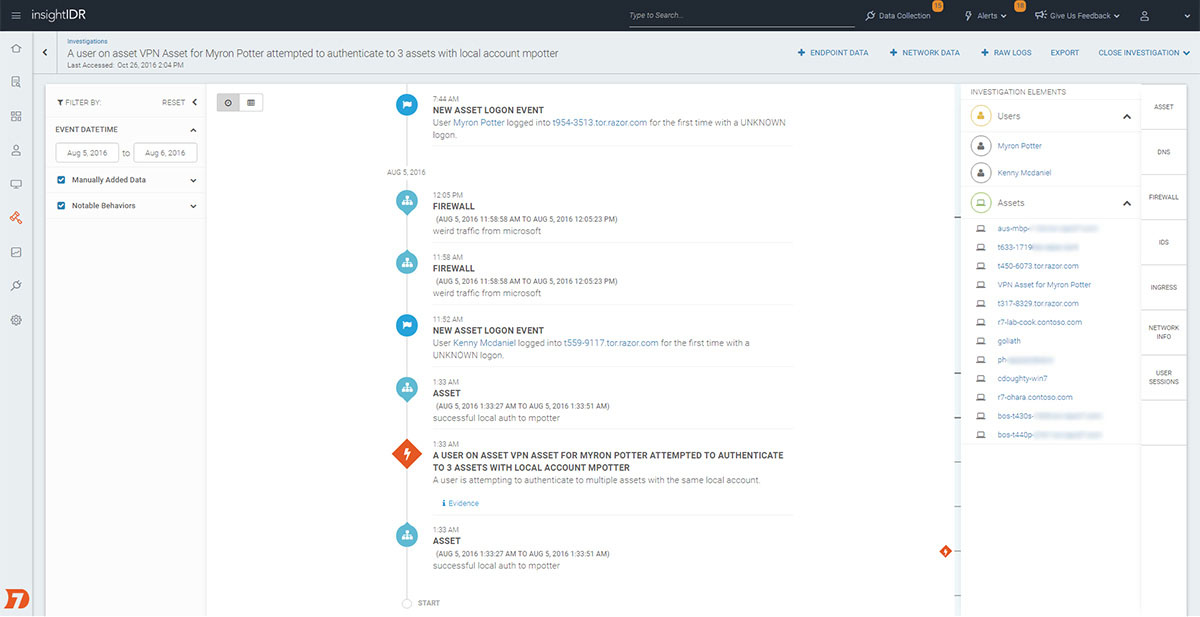
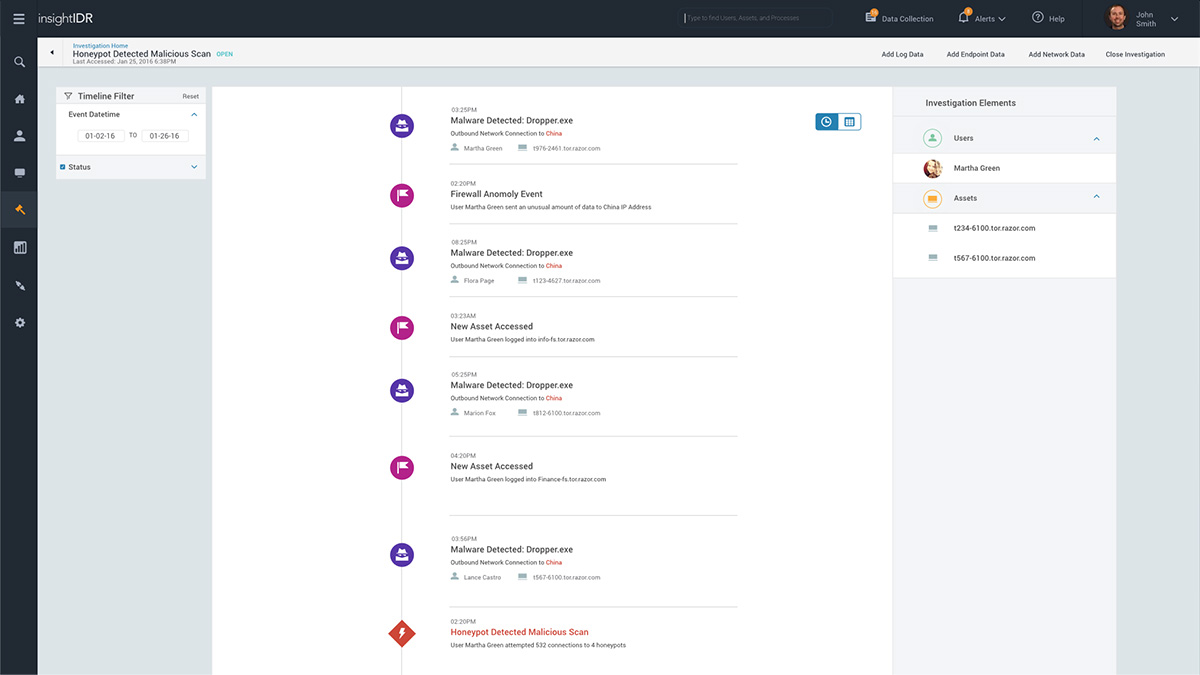
Visual Investigation Timeline
If you’re like the 62% of organizations that report getting more alerts than they can investigate, then you’re likely all too familiar with piecing together user activity, gathering endpoint data, and validating known good behavior just to uncover yet another false positive. InsightIDR unites log search, user behavior, and endpoint data in a single timeline to help you make smarter, faster decisions. How much faster? Customers report accelerating their investigations by as much as 20x.
Deception Technology
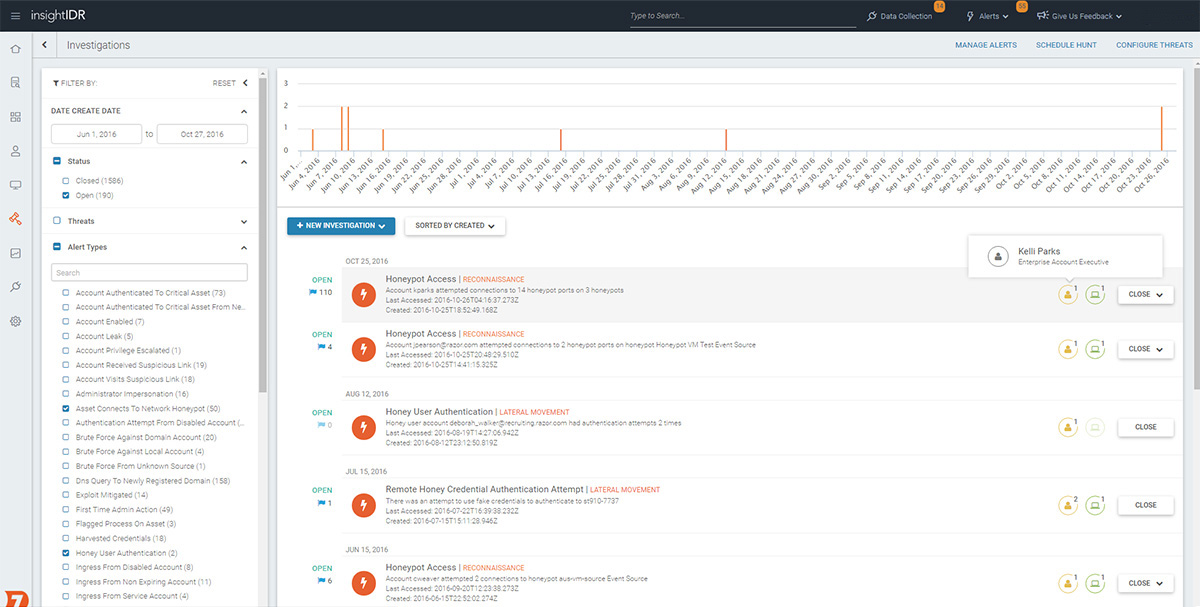
Monitoring solutions that only analyze log files leave traces of the attacker unfound. Through Rapid7's deep understanding of attacker behavior, InsightIDR provides not only UBA and endpoint detection, but easy-to-deploy intruder traps. These include honeypots, honey users, honey credentials, and honey files, all crafted to identify malicious behavior earlier in the attack chain.
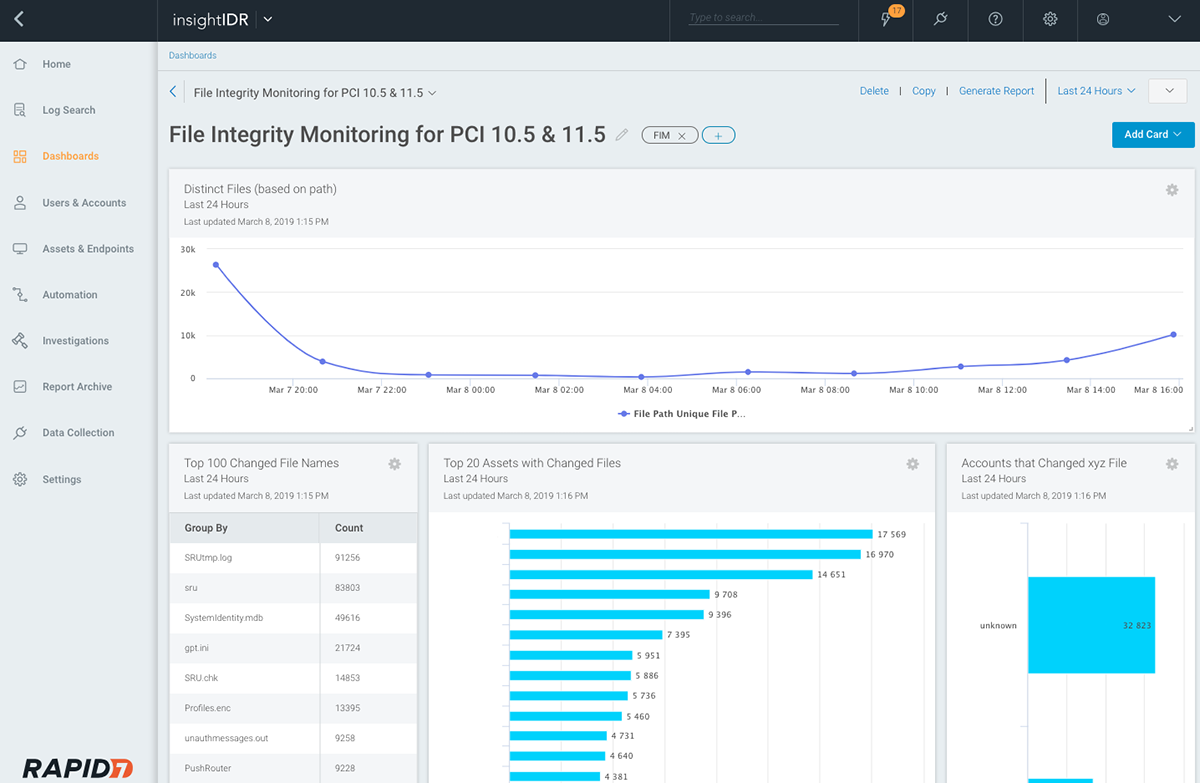
File Integrity Monitoring (FIM)
While InsightIDR excels at surfacing unknown attacks, it will also help you face a known challenge: demonstrating compliance across your security program. This includes audit logging and log management (e.g. PCI Requirement 10), user monitoring (e.g. NIST CSF Detect), and now, file integrity monitoring (FIM), a regulation mandated across PCI, HIPAA, and GDPR.
Once you deploy the included Insight Agent to your critical assets, you can activate file integrity monitoring to flag any changes to any specified files or directories on that endpoint.
Automation
To keep up with an ever-evolving environment, stay ahead of attackers, and combat the constraints of an under-resourced industry, security teams must find ways to improve efficiency in their security operations.
InsightIDR, offers a number of automation features to double down on these efficiencies. These include prebuilt workflows for things like containing threats on an endpoint, suspending user accounts, or integrating with ticketing systems. To further build on these capabilities, InsightIDR recently added enrichment via open source threat intelligence to this list of workflows, as well as the ability to trigger any of these workflows (or InsightConnect workflows) off of User Behavior Analytics (UBA) alerts.
No reviews found